ISPCONFIG Free Virus scanning
https://www.azcs.ca/wp-content/uploads/2023/07/ispconfig-virus-found-1024x507.png 1024 507 rdwild rdwild https://secure.gravatar.com/avatar/44bd259fbddc027551fcc75646fc9c2c?s=96&d=mm&r=gIf you are running ISPCONFIG to host client website and email at some point you are going to run across an infected website or two. As a host, you can encourage your clients to make sure their content management systems (joomla, wordpress) is regularly updating their code base and plugins. Keeping them updated is what is going to keep your hosts websites virus and trojen-free as hackers often target plugins which have security issues. It is important to stay vigilant when it comes to hackers that might want to use your website to do bad things … send out spam emails, attach other systems etc.
You could subscribe to a pay service that will provide a plugin to scan for Viruses and Trojens and the cost is quite reasonable.
https://ispprotect.com/
But there is another way … and its free!
Installing Clamwin (Ubuntu)
First – Update the installation
apt update -y
Then Install Clamwin
apt install clamav clamav-daemon -yYou should be able to check that clamwin is installed with the below command
clamscan -VThis should look something like: ClamAV 0.103.8/26984/Sat Jul 29 07:26:39 2023
Once clamwin is installed we next need to add our scanning script.
use your preferred editor (I use nano) to create “clamscan_daily.sh”
nano clamscan_daily.sh#!/bin/bash
LOGFILE_EMAIL="/var/log/clamav/clamav-email-$(date +'%Y-%m-%d').log";
LOGFILE_WEBSITES="/var/log/clamav/clamav-website-$(date +'%Y-%m-%d').log";
set HOST="$(hostname -f)"
EMAIL_FROM="clamav-daily@myinkbooks.com";
EMAIL_TO="rdwild@rayolightmedia.com";
DIRTOSCAN="/var/www";
EMAILTOSCAN="/var/vmail";
echo "Starting a daily scan of Websites";
for S in ${DIRTOSCAN}; do
DIRSIZE=$(du -sh "$S" 2>/dev/null | cut -f1);
echo "Starting a daily scan of "$S" directory.
Amount of data to be scanned is "$DIRSIZE".";
clamscan -ri "$S" >> "$LOGFILE_WEBSITES";
# get the value of "Infected lines"
MALWARE=$(tail "$LOGFILE_WEBSITES"|grep Infected|cut -d" " -f3);
# if the value is not equal to zero, send an email with the log file attached
if [ "$MALWARE" -ne "0" ];then
# using heirloom-mailx below
cat "$LOGFILE_WEBSITES" | mail -s "Malware Found on $HOST" "$EMAIL_FROM" "$EMAIL_TO";
fi
done
echo "\n";
echo "Starting a daily scan of email";
for S in ${EMAILTOSCAN}; do
DIRSIZE=$(du -sh "$S" 2>/dev/null | cut -f1);
echo "Starting a daily scan of "$S" directory.
Amount of data to be scanned is "$DIRSIZE".";
clamscan --remove yes -ri "$S" >> "$LOGFILE_EMAIL";
# get the value of "Infected lines"
MALWARE=$(tail "$LOGFILE_EMAIL"|grep Infected|cut -d" " -f3);
# if the value is not equal to zero, send an email with the log file attached
if [ "$MALWARE" -ne "0" ];then
# using heirloom-mailx below
cat "$LOGFILE_EMAIL" | mail -s "Malware Found on $HOST" "$EMAIL_FROM" "$EMAIL_TO";
fi
done
exit 0
You will notice a few parameters that need to be changed in the above code to change it for your needs. The first one is EMAIL_FROM and the second one is EMAIL_TO. If the above script finds a virus or trojen it sends and email using the from address to the email box in the email to address so both of those need to be changed for your system.
Once the clamscan_daily.sh script has been created it needs to be made executable.
chmod +x clamscan_daily.shOnce you have added the above script to your system you can test it using the below command to do a pilot run.
sudo ./clamscan_daily.shYou will notice that we use the sudo command here. The script needs to run as it would when running as a cron job which is the root user.
Once you have tested the script to make sure everything is working as it should you will need to add it to a daily cron job so that it runs every day.
I’m currently doing this by moving the script into the /etc/cron.daily folder.
sudo mv clamscan_daily.sh /etc/cron.daily/clamscan_daily.shIf the script finds something you will see an email similar to the one below
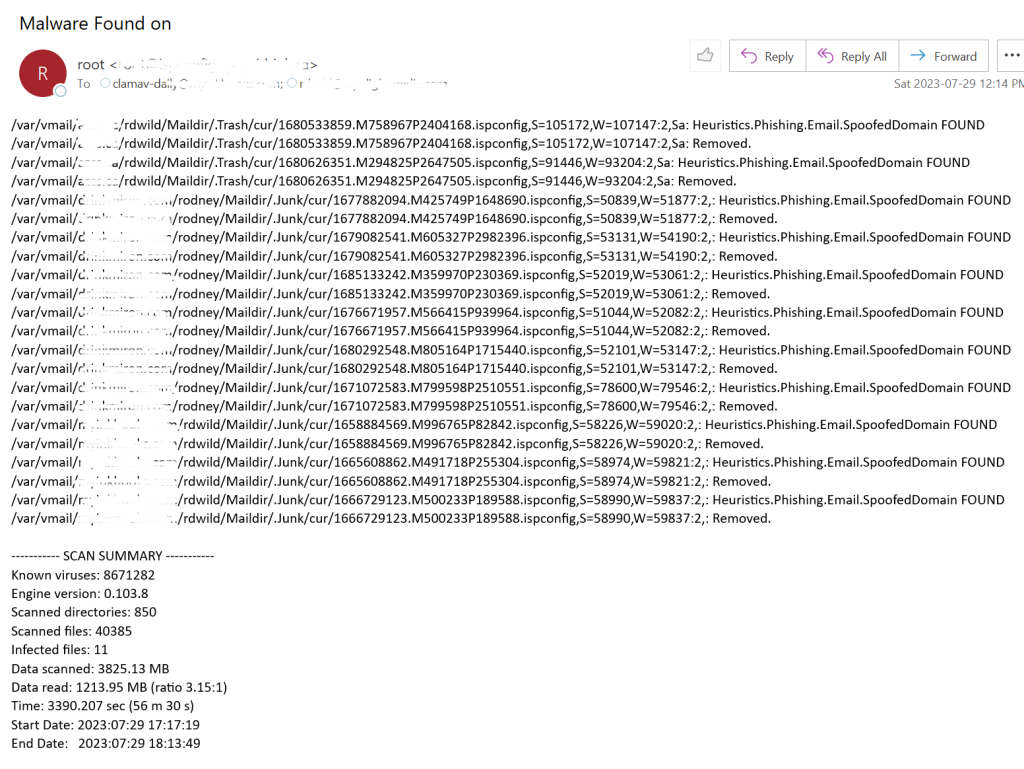
You will notice in the above email that nothing was found for websites (or they would have been listed here), but there were some spoofing emails that were found in the junk and trash folder. These were caught by other means and moved to trash but Clamav removed them. You will also notice that I obfuscated some of the text so I don’t get a bunch of junk emails.
Links
https://clamwin.com/ (main project website for clamwin)